Privacy Vulnerabilities in iOS Apps using In-App Browsers

Apple iOS 14 onwards has introduced the App Tracking Transparency (ATT), an opt-in privacy framework. Apps need to seek users' explicit consent before collecting and tracking their data. When you install or update an app, you are shown the Permissions screens where you give this consent. It gives users full control over what information the app can access and track. However, if an iOS app is using a custom in-app browser to open external links, this poses privacy and security vulnerabilities. In this article, we discuss:
- Why does this in-app browser scenario pose privacy threats?
- How you can detect if any extra code is being injected by the app?
- What are the best practices for various stakeholders to prevent such misuse?
- Which apps are using the best practices, and which ones are still lagging behind?
Why is it unsafe for the users if any app is using its own custom in-app browser?
The native code used by iOS apps has to follow Apple's App Tracking Transparency privacy framework. Thus, all the data tracking and collection happening within the iOS apps is approved by the user. However, in cases where the apps open external links to third-party websites, it is a different matter altogether.
There are two primary factors that can be a source of concern:
- Custom-built In-App Browsers
- WKContentWorld
Custom-built In-App Browsers
Generally, iOS apps open third-party links in the user's default browser. Or, they can use the SFSafariViewController, which is approved by Apple, to open websites within the apps. Both these cases are safe for the user's data privacy, because they prevent the iOS apps from monitoring any user actions happening on the external websites.
But, if an iOS app is using its own custom-built inapp browser, then it is within the power of that app to inject JavaScript code. Once this potential for code injection is left open, it becomes a possible source for malicious or illegal data tracking. Note that the addition of such JavaScript code can be done only by the developers of those iOS apps.
This extra JavaScript code can include tracking of keystrokes, tapping on-screen, elements selection, scrolling etc. Thus, it leaves open the possibility that some iOS apps could exploit this loophole to track and collect user actions data on external websites. Technically, such monitoring of user activity on third-party websites is no different from keylogging and spying. That's why this issue is worth highlighting and solving.
WKContentWorld
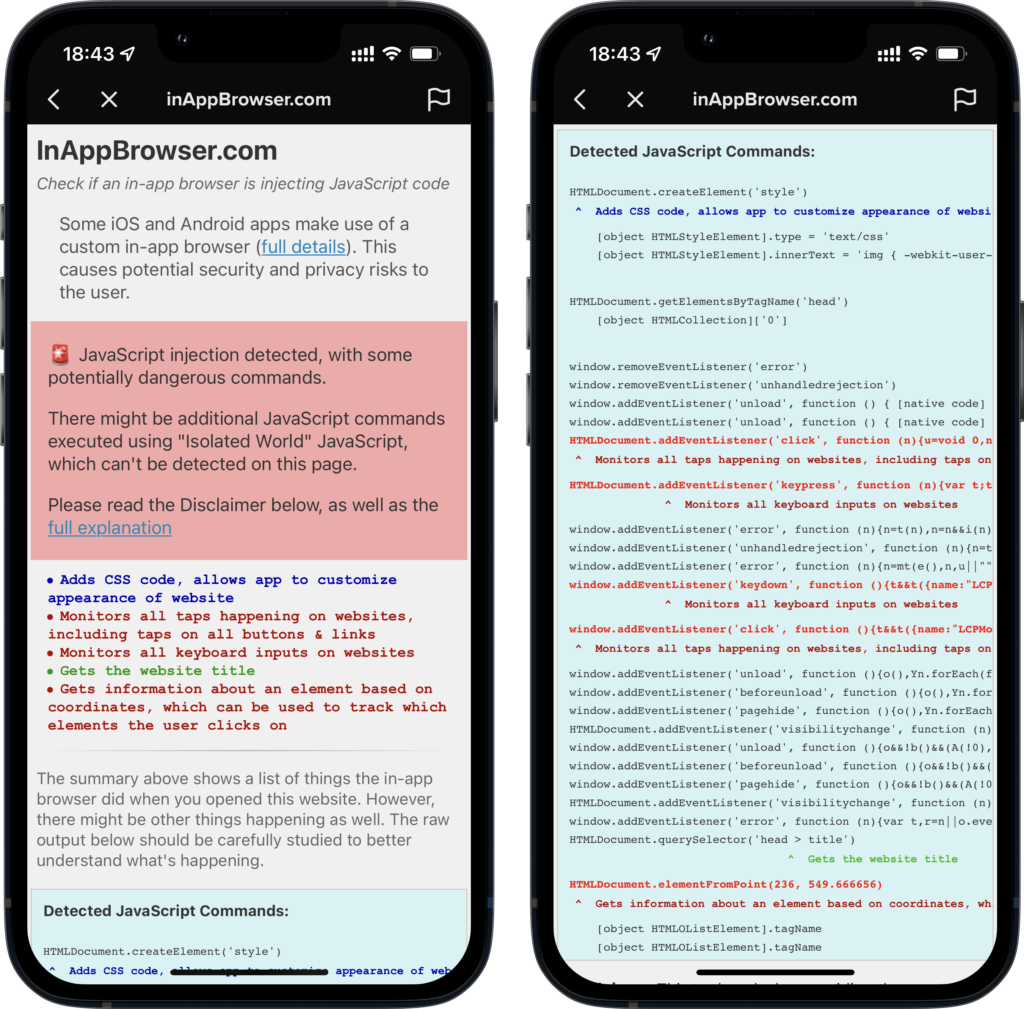
As we will see in the next section, it is possible to detect and figure out if any iOS app is injecting JavaScript code that monitors user actions. We can do that using an open-source project called inappbrowser.com. However, even such detection can be hidden by the iOS apps, if they choose to use WKContentWorld isolated JavaScript system. This method essentially separates the environments where any code is running. The inappbrowser project is unable to detect any JavaScript code injection if the iOS app is using WKContentWorld.
Thus, the best way forward to ensure data privacy and security is to follow best practices for opening third-party links from iOS apps. We will discuss these as well in the subsequent sections.
How to detect what JavaScript code is being injected by iOS apps to the third-party websites?
A useful open-source project by Felix Krause can detect when iOS apps are injection additional JavaScript code to third-party webpages. This is how to use it:
- Open any iOS app.
- Share a link to inappbrowser.com inside the app. It can be sent as a social media post, comment, or a DM.
- Click on the link.
- This will open the open-source website, detect if the iOS app is injecting any JavaScript, and list that code for you to see.
- But note that if the iOS app is using WKContentWorld for isolating JavaScript, then this inappbrowser tool will be unable to detect the JavaScript.
- Also, there is no way for us to check how these iOS apps are using the data that can be collected with such JavaScript.
- So, at best, we can only check if an iOS app is not using the best practices for privacy (by injecting some JavaScript to third-party websites opened inside it). Thus, it is only a basic diagnostic tool.
However, the discovery of this vulnerability, and the demo of this diagnostic tool shed a spotlight on what the best practices ought to be. Let's discuss them next.
What are the best practices for various stakeholders to prevent any misuse of custom in-app browsers?
The various stakeholders in this iOS app ecosystem are:
- Apple
- iOS app companies and developers
- Users
Apple's role in iOS privacy guidelines
Apple needs to enforce stricter privacy guidelines to the iOS Developer Community. They must discourage use of in-app browsers and include these instructions inside their ATT (App Tracking Transparency) framework. Further, they should encourage companies and developers to use best practices that will protect users' data privacy and security.
Best Practices for iOS app companies and developers
The best practices that iOS app developers can follow include:
- Using default browsers for opening third-party links from iOS apps.
- Using SFSafariViewController webview to open third-party external websites inside the iOS apps. This is authorized by Apple and doesn't allow any JavaScript code injection.
- Only for their own internal links and websites, the apps can use custom inapp browsers. This is because they have already obtained user permission to collect and track data within their own ecosystem. It also allows them to give the users a unified and frictionless experience between a company's iOS app and their own website.
- Companies can also specifically highlight that they are using best practices for safeguarding user privacy. This will enable them to utilize their transparency for marketing strategies and win users' trust in their brand.
Best Practices for iOS App Users while opening third-party websites from apps
Users need to be aware of what options they have while using iOS apps to secure their privacy. They should also have the awareness of which apps might be exploiting loopholes.
- Users should look for options to open links in their default browser. Usually, iOS apps show a window letting users decide how to view the external link.
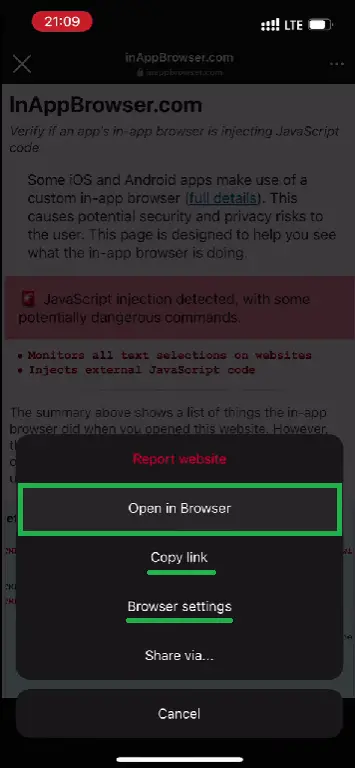
- If such a window isn't given, users should first open the third-party website in the in-app browser. But then, instead of using the website and entering any information, they should tap on the three dots on top-right. And either copy the link for pasting in your favorite browser, or directly open the link in Safari.
- Users can also try to long-press on links, copy them and then paste them in their favorite browser app.
- Users should use the diagnostic tool inappbrowser.com as explained above. This will let them get awareness of any potential privacy vulnerabilities in their favorite iOS apps.
- If some app is not letting users exercise privacy-friendly options to open external links, they can avoid using such apps. And they can post suggestions to the customer support and product review pages of these apps to use best practices for in-app privacy.
Which iOS apps are using the best practices, and which ones are still lagging behind?
Apart from developing the inappbrowser.com, Felix Krause has also tested some popular iOS apps. From his testing and reports, we are able to share the apps which follow best practices while opening third-party websites. And we can also see which apps can do better.
Popular apps that are using users' default browser or SFSafariViewController to open external sites (Best Practices | Safe)
Twitter, Reddit, WhatsApp, Slack, Google Maps, Youtube, Gmail, Telegram, Signal, Tweetbot, Spotify, Venmo, Microsoft Teams, Microsoft Outlook, Microsoft OneNote, Twitch.
Popular apps that use in-app browsers and inject some JavaScript code to third-party websites (Lagging Behind | Vulnerable)
- Tiktok
- FB Messenger
Official spokespersons for Tiktok and Meta have replied that they use such JavaScript to enhance user experience, debugging and troubleshooting. They have tried to assure the media that there is no malicious intent behind such code. However, as explained in this article, they can offer a good user experience and also collect user data with their permission by following the best practices.
Summary
Apple iOS apps must use default browser or SFSafariViewController while opening third-party links. When an app is using its own custom-built in-app browser, it is able to inject JavaScript code to the external sites. This may not mean any malicious intent, but it does leave the scope open for data privacy breaches. Hence, iOS developers must follow the best practices for opening links in their apps.
Users can detect instances of JavaScript code injection using the inappbrowser open-source diagnostic tool. They should also maintain an awareness of which iOS apps are following the best practices for data privacy and security, and which ones are still lagging behind.
What are your favorite iOS apps, and are they following best practices for user privacy while opening external websites? Let us know in the comments section below!